Architecture of Next Generation National Internet Infrastructure
Architecture of Next Generation National Internet Infrastructure
- The key steps to next generation national Internet infrastructure project are:
- Remove all copper networks and exchanges and replace them with Data Centers
- Install symmetric gbit fiber to all customers
- Convert all signal handling equipment to FPGA software synthesized networks
- Own all your FPGA software
- This visionary system removes all security issues of foreign governments interfering in local communications systems as more dependency is transferred into it for 5G and beyond.
How to manage change
- If any incumbent and their architects are voicing concerns about change and not being able to be ready with it, then give them time limits and funds to change if their accounts prove they need additional investment.
- The funds made available should be according to best practice of fiber install and not according what the companies claim their (inflated) costs are.
- If they haven't changed within their allotted time and the funding they received, remove their operating licenses.
- If they mount speculative legal challenges, they would be liable for all costs and further fines for delay tactics.
FPGA Softare Define Networks
- Information travels from A to B as on off light pulses.
- Light can turn on and off very fast - gbits, terabits, etc are not a problem.
- The pulsating light arrives at a Data Center and is converted to electrical ON/OFF signals using a fiber optic SFP module.
- The pulsating electrical signals need to be routed from the SFP module to their destinations and for that they enter an FPGA chip.
- There is coded within the signals information about how to route the packet.
- To make sense of it all, the on off signals are grouped into a packet of well defined on/off signals.
- These packets are opened by high speed electronics in the FPGA chip and its messages read, and then the packet is routed to the correct output ports.
- This process of opening packet and routing it can take place many times within the Data Center, until the packet is ready to leave the Data Center.
- When it leaves the Data Center, it leaves through an SFP module where it is converted from electrical signal to optical signal with a laser, and into another fiber which connects to other customers or other Data Centers.
- How the packet is opened, its messages read and then routed inside the Data Center is down to the FPGA software running inside the FPGA chips.
- There are various languages for writing this software such as Verilog and VHDL to name a few.
- Immediately you can judge that at the national level, the supplier of FPGA chips and boards are harmless and so too the SFP modules, but the software running in the FPGA needs to be your own and fully under your own control.
- To get infrastructure right, you need to ensure that harmful telecom equipment with its own packet opening, inspection and routing software is kept out of your core telecom infrastructure and this applies to all telecom operators who implement national infrastructure.
- Anything in the core network that opens packets for inspection or for routing is a national security threat if the software for doing this is not under your full control.
- When passing telecom laws, you should have all your equipment certified and classed as passive equipment such as SFP modules and FPGA cards, and active equipment where there is software running already that opens packets and routes packets.
- For national security you want to make sure all packet routing routing is 100% running your own software.
Access to FPGA software
- The software for FPGA should be open sourced and shared if you cannot obtain it at low enough cost.
- Fund universities to create open sourced FPGA software and train engineers to make it work.
- Never trust any routing software written by others for your core infrastructure until it has been fully vetted and ideally open sourced, and then customized to remove all security issues.
Dealing With Stubborn Telecom Companies
- There will be no end of stubborn telecom companies (sponsored by foreign governments with threats like we won't share intelligence if you don't buy from our country) insisting their software and hardware is proprietary and cannot be separated.
- Their will and modus operandi needs to be broken, and this needs to be made clear to them at all times.
- All the noise they make is just a ruse to sneak in equipment that opens packets and routes them to their own design leaving in vulnerabilities for foreign control of telecom infrastructure.
- The simplest solution is to create a national scheme to register FPGA cards (without software), and modules such as SFP that do not need to open packets or route packets.
- Then invite everyone from academics to private companies to fill the market opportunity to supply passive FPGA cards and SFP modules.
- Invite your own academics and telecom companies to fill the FPGA cards with software to your exacting security needs.
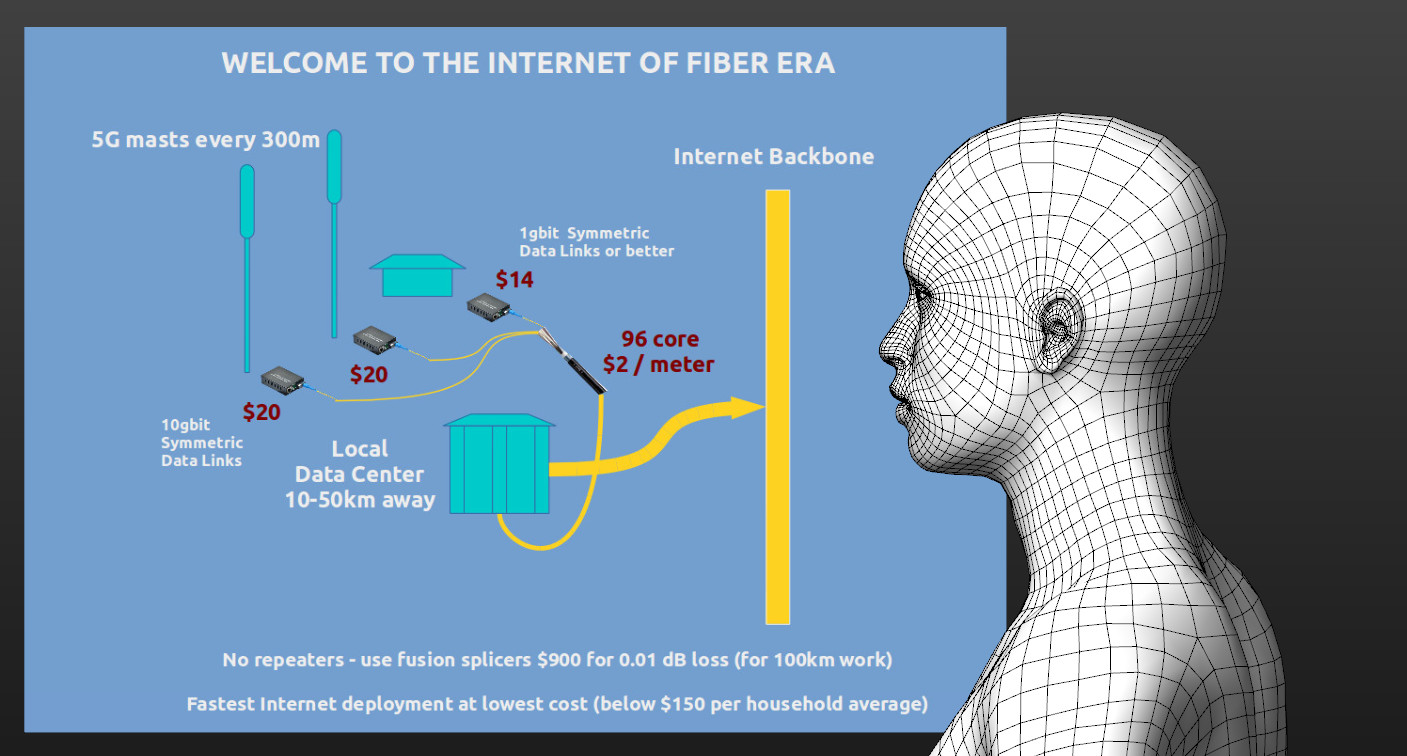
The Internet of Fiber Architecture
- We are Internet whisperers and showing you the architecture of The Internet of Fiber system long before it is built.
- Telecom incumbents should be asked to convert to cheap fiber infrastructure or become customers of Data Center based providers of connectivity.
More